10 Best Vulnerability Management Tools In 2025
- С сайта: Vulnerability(cybersecuritynews.com)
- Вернуться к списку новостей
10 Best Vulnerability Management Tools In 2025
Author: Cyber Writes TeamIn today’s rapidly evolving digital landscape, vulnerability management has become a cornerstone of effective cybersecurity.
As organizations expand their digital footprint across cloud, on-premises, and hybrid environments, the need for robust vulnerability management tools is more critical than ever.
These solutions not only help identify security weaknesses but also prioritize risks, automate remediation, and ensure compliance with regulatory standards.
Choosing the right vulnerability management tool can be overwhelming, given the sheer number of options and the complexity of modern IT environments.
The best tools in 2025 offer a blend of continuous monitoring, intelligent automation, seamless integration, and actionable reporting.
They empower security teams to stay ahead of emerging threats, reduce attack surfaces, and maintain a proactive security posture.
This comprehensive guide reviews the top 10 vulnerability management tools in 2025 , providing detailed insights into their specifications, reasons to buy, and standout features.
Whether you’re an enterprise, SMB, or security professional, this article will help you make an informed decision to strengthen your organization’s security framework.
Comparison Table: Top 10 Vulnerability Management Tools (2025)
ToolContinuous MonitoringCloud SupportAutomationReportingIntegrationFireCompassYesYesYesYesYesTenable NessusYesYesYesYesYesQualys VMDRYesYesYesYesYesRapid7 InsightVMYesYesYesYesYesIntruderYesYesYesYesYesAcunetixYesYesYesYesYesBurp SuiteYesYesYesYesYesOpenVASYesYesNoYesYesTripwire IP360YesYesYesYesYesNmapNoNoNoYesYes
1. FireCompass

FireCompass is a next-generation vulnerability management platform designed for organizations seeking proactive security.
It leverages Continuous Automated Red Teaming (CART) to discover, assess, and prioritize vulnerabilities in real time.
FireCompass combines offensive and defensive strategies, providing a holistic view of your attack surface and enabling rapid remediation before attackers can exploit weaknesses.
Its integration with DevSecOps pipelines ensures vulnerabilities are addressed early in the development lifecycle, reducing risk and improving operational resilience.
FireCompass stands out for its ability to map assets automatically, identify exploitable vulnerabilities specific to your environment, and offer actionable insights.
Its seamless integration capabilities and advanced analytics make it a top choice for security teams aiming for comprehensive, continuous protection.
Specifications
- Deployment: Cloud-based, SaaS
- CART integration for automated red teaming
- Real-time vulnerability discovery and prioritization
- DevSecOps and CI/CD pipeline support
- API integrations with SIEM, ITSM, and ticketing tools
Reason to Buy
- Proactive, continuous attack surface monitoring
- Automated red teaming for real-world threat simulation
- Seamless integration with existing security workflows
- Actionable insights for rapid remediation
Features
- Real-time asset discovery and mapping
- Risk-based vulnerability prioritization
- Automated and manual remediation guidance
- Comprehensive reporting and analytics
 Best For: Organizations seeking advanced, proactive vulnerability management.
Best For: Organizations seeking advanced, proactive vulnerability management.🔗Try FireCompass here→FireCompass Official Website
2. Tenable Nessus
.webp)
Tenable Nessus is an industry-leading vulnerability assessment tool trusted by security professionals worldwide.
Known for its comprehensive scanning capabilities and low false positive rates, Nessus supports diverse platforms, including cloud, on-premises, and IoT devices.
Its extensive plugin library ensures up-to-date detection of the latest vulnerabilities, while customizable reporting and compliance checks help organizations meet regulatory requirements.
Nessus is user-friendly, making it accessible for both small teams and large enterprises.
Its integration with other Tenable products and third-party tools enables a unified approach to vulnerability management, ensuring that security teams can quickly identify, prioritize, and remediate risks across their entire infrastructure.
Specifications
- Deployment: On-premises, cloud, hybrid
- Supports CVSS v4, EPSS, and Tenable VPR scoring
- Customizable scan templates and schedules
- Compliance checks for major standards (PCI, HIPAA, etc.)
- Integration with SIEM and ticketing systems
Reason to Buy
- Industry-leading vulnerability detection accuracy
- Flexible deployment for diverse IT environments
- Extensive compliance and configuration auditing
- Scalable for organizations of all sizes
Features
- Comprehensive vulnerability scanning
- Real-time risk scoring and prioritization
- Automated compliance reporting
- Integration with third-party security tools
 Best For: Enterprises needing reliable scanning across large infrastructures.
Best For: Enterprises needing reliable scanning across large infrastructures.🔗Try Tenable Nessus here→Tenable Nessus Official Website
3. Qualys VMDR

Qualys VMDR (Vulnerability Management, Detection, and Response) is a unified platform that combines asset discovery, vulnerability assessment, threat prioritization, and remediation workflows.
Its cloud-native architecture ensures scalability, making it ideal for organizations with complex, distributed environments.
Qualys VMDR offers continuous monitoring and automated patching, helping security teams stay ahead of emerging threats.
The platform’s advanced risk scoring and comprehensive reporting capabilities provide actionable intelligence, enabling organizations to prioritize vulnerabilities based on business impact.
Its seamless integration with ITSM and SIEM tools streamlines remediation and compliance processes.
Specifications
- Deployment: Cloud-native, SaaS
- Unified asset inventory and vulnerability detection
- Automated patch management
- Risk-based vulnerability prioritization
- Integration with ITSM, SIEM, and CMDB platforms
Reason to Buy
- All-in-one vulnerability management solution
- Automated asset discovery and risk scoring
- Scalable for large, distributed enterprises
- Streamlined remediation and compliance workflows
Features
- Continuous asset and vulnerability monitoring
- Automated detection and response
- Customizable dashboards and reports
- Integration with security and IT operations tools
 Best For: Organizations requiring an all-in-one, scalable solution.
Best For: Organizations requiring an all-in-one, scalable solution.🔗Try Qualys VMDR here→Qualys Official Website
4. Rapid7 InsightVM

Rapid7 InsightVM delivers real-time visibility into your organization’s attack surface, leveraging dynamic asset discovery and AI-driven risk prioritization.
Its flexible scanning options agent-based or agentless ensure broad coverage across endpoints, cloud, and on-premises environments.
InsightVM’s interactive dashboards and integration with IT remediation workflows streamline vulnerability management from detection to resolution.
The platform’s active risk scoring model factors in exploitability, attacker behavior, and business impact, helping teams focus on the most critical vulnerabilities.
With seamless integration into DevOps pipelines and SIEM tools, InsightVM supports modern security operations at scale.
Specifications
- Deployment: Cloud, on-premises, hybrid
- Agent-based and agentless scanning
- AI-driven risk prioritization
- Live dashboards and reporting
- Integration with SIEM, ITSM, and DevOps tools
Reason to Buy
- Real-time, dynamic attack surface visibility
- Intelligent risk-based vulnerability prioritization
- Automated remediation and workflow integration
- Scalable for complex, hybrid environments
Features
- Continuous asset discovery and scanning
- Customizable risk scoring and analytics
- Automated ticketing and remediation tracking
- Integration with security and IT operations platforms
 Best For: Enterprises seeking detailed risk assessments and compliance tracking.
Best For: Enterprises seeking detailed risk assessments and compliance tracking.🔗Try Rapid7 InsightVM here→Rapid7 Official Website
5. Intruder

Intruder offers a cloud-based vulnerability management solution with a focus on simplicity and automation.
Designed for SMBs and agile teams, Intruder provides continuous vulnerability scanning, real-time threat notifications, and automated reporting.
Its straightforward integration with existing workflows allows organizations to quickly identify and remediate vulnerabilities without complex setup.
Intruder’s user-friendly interface and actionable insights make it an excellent choice for organizations looking to enhance their security posture without the overhead of traditional enterprise tools.
Its focus on active threats and exploitability ensures that remediation efforts are prioritized for maximum impact.
Specifications
- Deployment: Cloud-based, SaaS
- Automated, continuous vulnerability scanning
- Real-time threat notifications
- Integration with Slack, Jira, and other tools
- Simple setup and management
Reason to Buy
- Easy-to-use platform for rapid onboarding
- Continuous monitoring with automated alerts
- Cost-effective for SMBs and startups
- Integration with popular collaboration tools
Features
- Scheduled and on-demand scans
- Real-time vulnerability alerts
- Automated remediation guidance
- Customizable reporting and dashboards
 Best For: SMBs looking for cost-effective, lightweight solutions.
Best For: SMBs looking for cost-effective, lightweight solutions.🔗Try Intruder here→Intruder Official Website
6. Acunetix
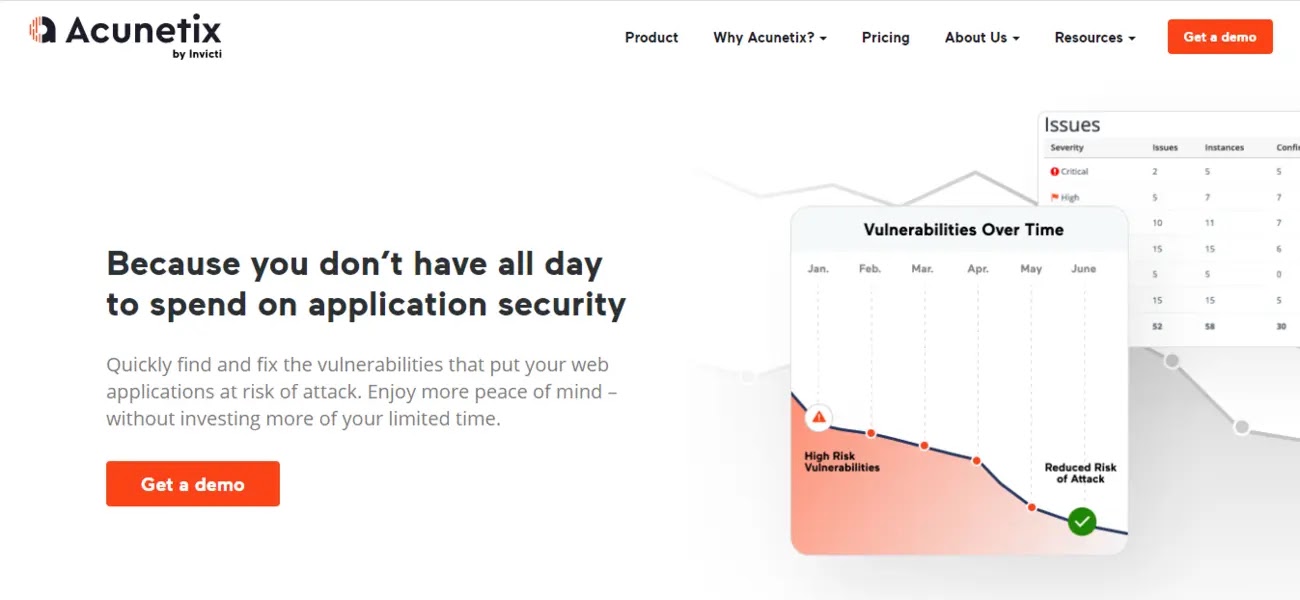
Acunetix specializes in web application and API security, offering comprehensive scanning for OWASP Top 10 vulnerabilities and more.
Its advanced crawler and scanner can handle complex web applications, including those built with JavaScript-heavy frameworks.
Acunetix integrates seamlessly with CI/CD pipelines, enabling secure development practices and reducing the risk of vulnerabilities in production.
The platform’s intuitive interface, detailed reporting, and remediation guidance make it a favorite among development and security teams.
Acunetix helps organizations safeguard their web assets and ensure compliance with industry standards.
Specifications
- Deployment: Cloud, on-premises
- Advanced web application and API scanning
- Integration with CI/CD and DevOps pipelines
- Comprehensive vulnerability database
- Customizable scan configurations
Reason to Buy
- Specialized focus on web application security
- Integration with development workflows
- Detailed vulnerability reports and remediation advice
- Supports complex and modern web technologies
Features
- Automated web and API scanning
- Detection of OWASP Top 10 and zero-day threats
- Integration with bug tracking and DevOps tools
- Customizable scan policies and scheduling
 Best For: Development teams prioritizing application security.
Best For: Development teams prioritizing application security.🔗Try Acunetix here→Acunetix Official Website
7. Burp Suite
.webp)
Burp Suite is a powerful platform for web application security testing, trusted by penetration testers and security professionals.
It offers both automated and manual testing capabilities, allowing users to uncover vulnerabilities that automated scanners might miss.
Burp Suite’s extensible architecture and robust suite of tools make it ideal for complex environments and in-depth security assessments.
With high customization and detailed reporting, Burp Suite supports both routine vulnerability scanning and advanced penetration testing.
Its integration with CI/CD pipelines and collaboration features streamline security testing throughout the software development lifecycle.
Specifications
- Deployment: Desktop, cloud
- Manual and automated vulnerability testing
- Extensible with plugins and custom scripts
- Integration with CI/CD pipelines
- Comprehensive reporting and analysis
Reason to Buy
- Industry-leading for manual web security testing
- Highly customizable for advanced users
- Supports integration with development pipelines
- Regular updates and strong community support
Features
- Automated and manual web vulnerability scanning
- Advanced testing tools (intruder, repeater, sequencer)
- Extensible with BApp Store plugins
- Detailed vulnerability reporting
 Best For: Security professionals conducting in-depth manual testing.
Best For: Security professionals conducting in-depth manual testing.🔗Try Burp Suite here→Burp Suite Official Website
8. OpenVAS
.webp)
OpenVAS is a free, open-source vulnerability scanner developed by Greenbone Networks.
It provides comprehensive scanning for networks, systems, and applications, with support for both authenticated and unauthenticated scans.
OpenVAS’s regularly updated vulnerability feeds ensure detection of the latest threats, while its customizable scan configurations cater to diverse security needs.
Ideal for organizations with in-house expertise, OpenVAS offers flexibility and control without the cost of commercial solutions.
Its integration capabilities and extensive vulnerability database make it a valuable tool for technical teams on a budget.
Specifications
- Deployment: On-premises, Linux-based
- Open-source (GPL-2.0 license)
- Supports over 26,000 CVEs
- Customizable scan configurations
- Integration with security and reporting tools
Reason to Buy
- Free and open-source with no licensing costs
- Extensive vulnerability coverage and regular updates
- Flexible for technical, hands-on teams
- Customizable scanning for diverse environments
Features
- Network, system, and application scanning
- Authenticated and unauthenticated scans
- Regularly updated vulnerability feeds
- Integration with reporting and SIEM tools
 Best For: Budget-conscious organizations with in-house expertise.
Best For: Budget-conscious organizations with in-house expertise.🔗Try OpenVAS here→OpenVAS Official Website
9. Tripwire IP360

Tripwire IP360 is an enterprise-grade vulnerability management solution known for its comprehensive coverage and compliance support.
It provides continuous monitoring, automated remediation workflows, and detailed reporting tailored to regulatory standards.
Tripwire IP360’s asset discovery and risk prioritization help organizations focus remediation efforts where they matter most.
With its scalable architecture and integration with IT and security operations tools, Tripwire IP360 is well-suited for large organizations with stringent compliance requirements.
Its ability to deliver actionable insights and support regulatory audits makes it a trusted choice for security-conscious enterprises.
Specifications
- Deployment: On-premises, hybrid
- Continuous asset discovery and vulnerability scanning
- Automated remediation workflows
- Compliance reporting for major standards
- Integration with ITSM and SIEM platforms
Reason to Buy
- Enterprise-grade vulnerability management
- Strong compliance and regulatory support
- Automated workflows for efficient remediation
- Scalable for large, complex environments
Features
- Continuous vulnerability and asset monitoring
- Risk-based prioritization and analytics
- Automated compliance and audit reporting
- Integration with security operations tools
 Best For: Enterprises with stringent compliance requirements.
Best For: Enterprises with stringent compliance requirements.🔗Try Tripwire IP360 here→Tripwire Official Website
10. Nmap
.webp)
Nmap is a widely used open-source tool for network discovery and security auditing.
While not a full-featured vulnerability management platform, Nmap excels at identifying open ports, services, and network devices, providing valuable insights for network-level assessments.
Its scripting engine enables advanced scanning and detection of specific vulnerabilities.
Nmap’s lightweight design and robust community support make it a staple for network administrators and security professionals.
It’s best used as a complementary tool alongside dedicated vulnerability management solutions.
Specifications
- Deployment: Cross-platform (Windows, Linux, macOS)
- Open-source (GPL license)
- Network discovery and service enumeration
- Scripting engine for advanced scans
- Integration with other security tools
Reason to Buy
- Free and widely supported across platforms
- Powerful for network discovery and auditing
- Extensible with custom scripts
- Lightweight and easy to use
Features
- Network and port scanning
- Service and OS detection
- Scriptable vulnerability checks
- Integration with security toolchains
 Best For: Network-level vulnerability assessments.
Best For: Network-level vulnerability assessments.🔗Try Nmap here→Nmap Official Website
Conclusion
Selecting the right vulnerability management tool is essential for building a resilient cybersecurity strategy in 2025.
The top tools reviewed here provide a range of capabilities from continuous monitoring and automated remediation to compliance support and advanced analytics.
Whether you’re a large enterprise, a growing SMB, or a security specialist, these solutions offer the flexibility, scalability, and intelligence needed to safeguard your digital assets.
As cyber threats continue to evolve, investing in a robust vulnerability management platform will help your organization stay one step ahead.
Prioritize tools that align with your operational needs, integrate seamlessly with your existing workflows, and deliver actionable insights to drive effective risk management.
With the right solution in place, you can confidently protect your infrastructure, ensure compliance, and support your business’s ongoing digital transformation.
#Cyber_Security #Cyber_Security_News #Top_10 #Vulnerability #top_10 #vulnerability #vulnerability_assignment #Vulnerability_Management_Tools
Оригинальная версия на сайте:


