Detecting Zero-Day Vulnerabilities in .NET Assemblies With Claude AI
- С сайта: Vulnerability(cybersecuritynews.com)
- Вернуться к списку новостей
Detecting Zero-Day Vulnerabilities in .NET Assemblies With Claude AI
Author: Tushar Subhra DuttaCybersecurity researchers have achieved a significant breakthrough in automated vulnerability detection by successfully leveraging Claude AI to identify zero-day exploits in .NET assemblies.
This innovative approach combines artificial intelligence with reverse engineering techniques to discover previously unknown security flaws in Microsoft-signed binaries, potentially revolutionizing how security professionals hunt for vulnerabilities at scale.
The research demonstrates how Model Context Protocol (MCP) can be integrated with Claude AI to provide automated analysis capabilities for .NET assemblies.
This methodology represents a paradigm shift from traditional manual code review processes, offering the potential for rapid identification of security vulnerabilities across large codebases.
.webp) Build Error for ilspycmd-docker (Source – Trustedsec)
Build Error for ilspycmd-docker (Source – Trustedsec)TrustedSec researchers noted that the AI successfully identified critical deserialization vulnerabilities in System.AddIn.dll, a component that ships with Windows by default.
The vulnerability centers around unsafe BinaryFormatter usage in the AddInStore.cs file, where the ReadCache and WriteCache methods perform serialization and deserialization operations without proper security controls.
This flaw had been previously documented but served as an excellent test case for evaluating Claude’s analytical capabilities.
The research findings reveal that Claude not only detected the known vulnerability but also traced complete exploitation paths from user-controlled input to the vulnerable deserialization calls.
The AI identified multiple attack vectors through AddinUtil.exe, including both the -addinroot and -pipelineroot command-line parameters that could lead to arbitrary code execution when processing malicious cache files.
Advanced Exploitation Path Analysis
The most compelling aspect of this research lies in Claude’s ability to construct detailed exploitation scenarios and generate functional proof-of-concept code.
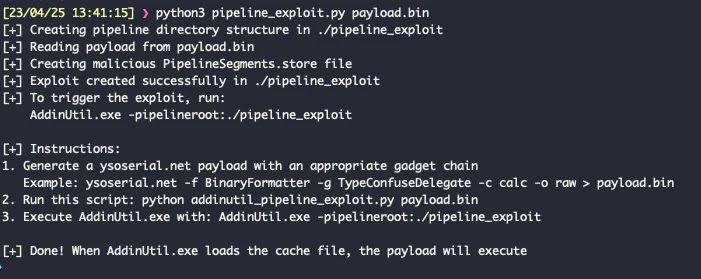.webp) Running the Proof-of-Concept Code (Source – Trustedsec)
Running the Proof-of-Concept Code (Source – Trustedsec)When analyzing the -pipelineroot attack vector, Claude traced the execution flow from command-line arguments through multiple method calls to reach the vulnerable BinaryFormatter.Deserialize() function.
The AI correctly identified that the vulnerability occurs when AddinUtil.exe calls either AddInStore.Update() or AddInStore.Rebuild() methods, which eventually invoke GetPipelineDeploymentState() and subsequently trigger the unsafe deserialization.
Claude’s analysis revealed that successful exploitation requires creating a malicious PipelineSegments.store file within a specific directory structure containing HostSideAdapters, Contracts, AddInSideAdapters, and AddInViews subdirectories.
The AI generated Python code that properly formats the exploit payload with the necessary 12-byte header structure expected by the ReadCache method, demonstrating sophisticated understanding of the binary file format requirements.
BinaryFormatter binaryFormatter = new BinaryFormatter(); result = (T) binaryFormatter.Deserialize(stream);
The generated exploit code successfully created the required directory structure and properly formatted cache files that, when processed by AddinUtil.exe, resulted in arbitrary code execution.
This achievement validates the potential for AI-assisted vulnerability research to not only identify security flaws but also develop working exploits with minimal human intervention.
The implications of this research extend beyond academic interest, suggesting that automated AI-driven vulnerability discovery could significantly accelerate the identification of zero-day exploits in enterprise software environments.
As cybersecurity teams face increasing pressure to identify and remediate vulnerabilities quickly, this methodology offers a promising approach to scaling security research efforts while maintaining the analytical depth traditionally requiring manual expert review.
#Cyber_Security_News #Vulnerability #cyber_security_news #vulnerability
Оригинальная версия на сайте:


