LeakyCLI: New Vulnerability Exposes Credentials In AWS, Azure & Google Cloud
- С сайта: Vulnerability(cybersecuritynews.com)
- Вернуться к списку новостей
LeakyCLI: New Vulnerability Exposes Credentials In AWS, Azure & Google Cloud
Author: EswarMultiple Cloud Service providers like Google Cloud, AWS, and Azure have been discovered with a new vulnerability that has been termed “LeakyCLI.”
As the name suggests, the Command line interfaces of Google Cloud (Gcloud CLI), AWS (AWSCLI), and Azure (Azure CLI) expose sensitive information in the form of environment variables.
This vulnerability was assigned with CVE-2023-36052, and the severity was given as 8.6 ( High ).
If this vulnerability is subjected to exploitation, threat actors can gain access to multiple sensitive information such as credentials, usernames, passwords, and keys that can later be used to gain access to any resource.
Exploitation can be done through tools like GitHub actions.
LeakyCLI: New Vulnerability
According to the reports shared with Cyber Security News, CLIs are tools provided by Cloud Service vendors for users to manage cloud services and use documented Rest API requests to gather information about configuration or other issues.
Free Live Webinar for DIFR/SOC Teams : Securing the Top 3 SME Cyber Attack Vectors -Register Here .
In addition, these CLIs are also used in CI/CD (Continuous Integration and Continuous Deployment) environments where the use of these documented Rest API requests can expose configuration information about the resources alongside environment variables.
In addition, all these issues exist in a serverless environment, such as Azure functions, Google Cloud functions, and AWS Lambda.
AWS CLI Leakage
In AWS, the lambda API requests like aws lambda get-function-configuration and aws lambda get-function can be used to gather information about the environment configuration and function information.
However, the output given to the stdout contains the environment variable information as well.
 AWS CLI Leakage (Source: Orca Security)
AWS CLI Leakage (Source: Orca Security)Some of the organizations store sensitive information such as AWS bucket name, passwords or any other keys in the environment variables which are exposed when running these commands on the AWS CLI.
GCloud CLI Leakage
Similar to AWS CLI, GCloud CLI also offers certain commands like gcloud functions deploy –set-env-vars and gcloud functions deploy –update-env-vars for accessing resources and configurations of the GCloud environment.
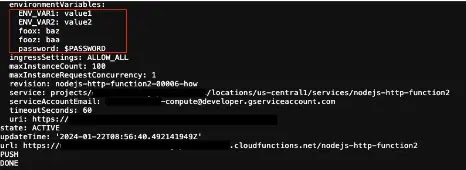 AWS CLI Leakage (Source: Orca Security)
AWS CLI Leakage (Source: Orca Security)However, the responses given in the stdout expose defined or predefined environment variables.
In some extreme cases, the stdout also contains build logs which could contain pre-existing environment variables or sensitive information such as passwords in the cloud function which are exposed.
Proof Of Concept
AWS
In order to prove this vulnerability’s existence and severity, researchers used the below command to leak information via GitHub actions, CircleCI and TravisCI
“aws lambda” AND (“update-function-configuration” OR “update-function-code” OR “publish-version”) AND (path:.github/workflows OR path:.circleci OR path:.travis)
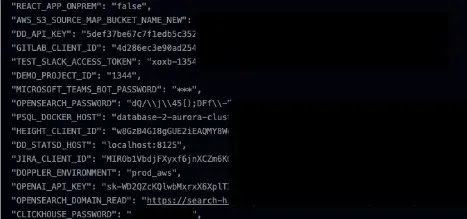 Leakage via GitHub Actions (Source: Orca Security)
Leakage via GitHub Actions (Source: Orca Security)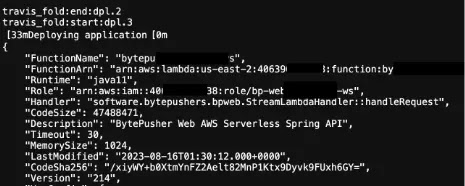 Leakage via TravisCI (Source: Orca Security)
Leakage via TravisCI (Source: Orca Security)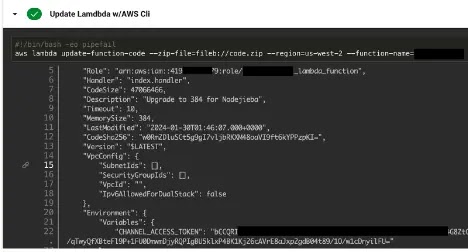 Leakage via CircleCI (Source: Orca Security)
Leakage via CircleCI (Source: Orca Security)The result of this command contained over 1000 hits which was narrowed down to many dozens of projects by manual and limited procedures.
Some of the resulting repositories consisted of logs that leaked sensitive information like environment variables, passwords and keys.
In other cases, other information like account ID’s or S3 bucket names were exposed which are not considered to be private.
Nevertheless, there were also cases where the sensitive information ranged between account IDs (not private) to passwords and keys (Private).
GCP
Researchers used the below command to test Google Cloud CLI to target Github Actions, CircleCI, TravisCI and Cloudbuild.
The resulting hits contributed to only 137 repositories but most of them consisted of several sensitive information such as project names, service accounts and environment variables.
“gcloud functions deploy” AND (“–set-env-vars” OR “–update-env-vars” OR “–remove-env-vars”) AND (path:.github/workflows OR path:.circleci OR path:.travis OR path:cloudbuild)
To provide a brief insight on how they were able to fetch cloudbuild logs of private repositories, researchers used cloudbuild GitHub integration application which allowed them to view these build logs inside GitHub.
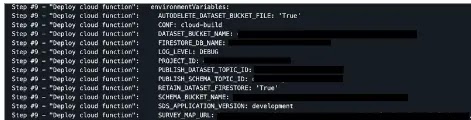 Leakage via Cloudbuild (Source: Orca Security)
Leakage via Cloudbuild (Source: Orca Security)If threat actors get their hands on these cloudbuild logs and gather these sensitive information, they can use them to escalate their privileges to other services using the exposed environment variables.
Mitigation
AWS
- Users of AWS are recommended to follow the below steps
- Do not use environment variables to store sensitive information
- Review build logs to make sure they don’t contain sensitive information
- Restrict the access and scope of the logs to specific use cases
GCP
For Google Cloud users, the output from the CLI can be suppressed by using the –no-user-output-enabled flag. Additionally, the use of the Secrets manager function is also recommended for storing credentials.
For Azure users, it is recommended to upgrade your CLI versions to the latest as a means of mitigating this vulnerability.
Looking to Safeguard Your Company from Advanced Cyber Threats? DeployTrustNetto Your Radar ASAP .
#cloud #Cyber_Security #Vulnerability #cloud_security #cyber_security #cyber_security_news #Vulnerability_Disclosure
Оригинальная версия на сайте:


